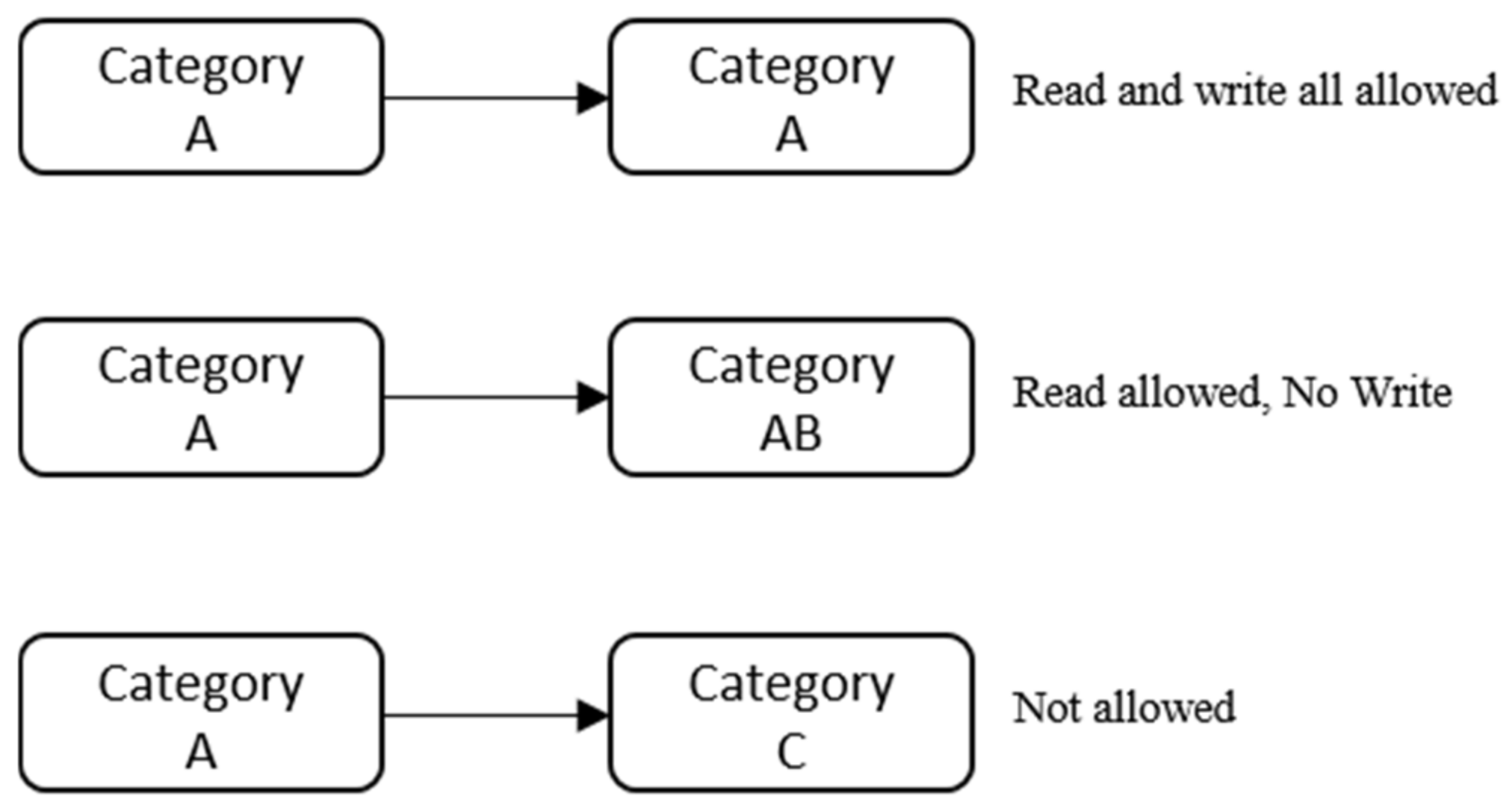
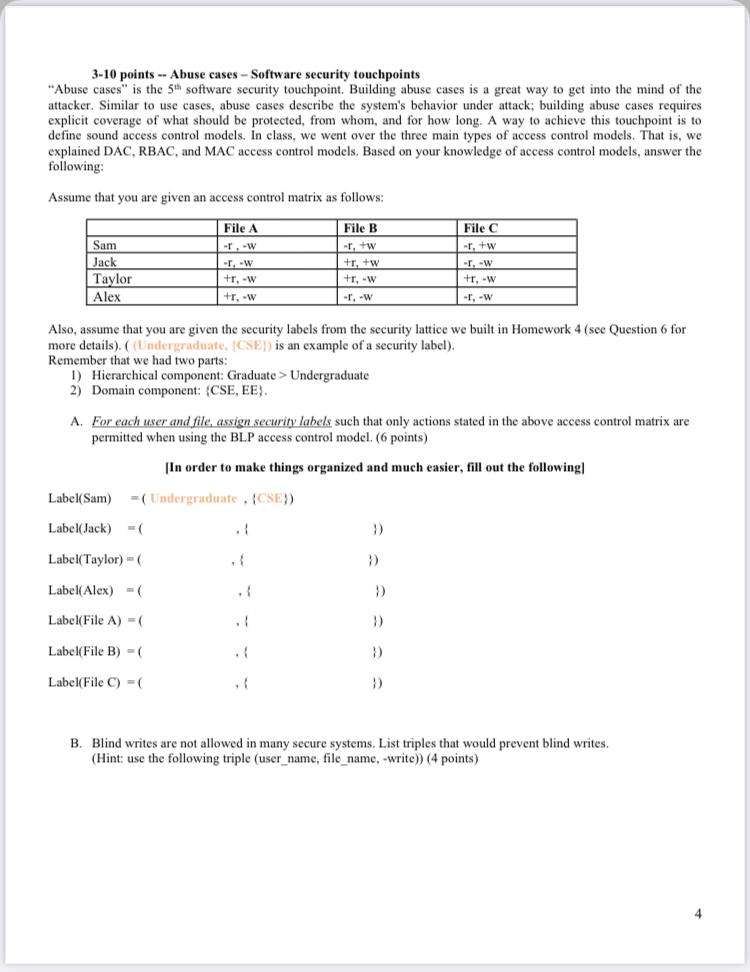
44 security labels access control
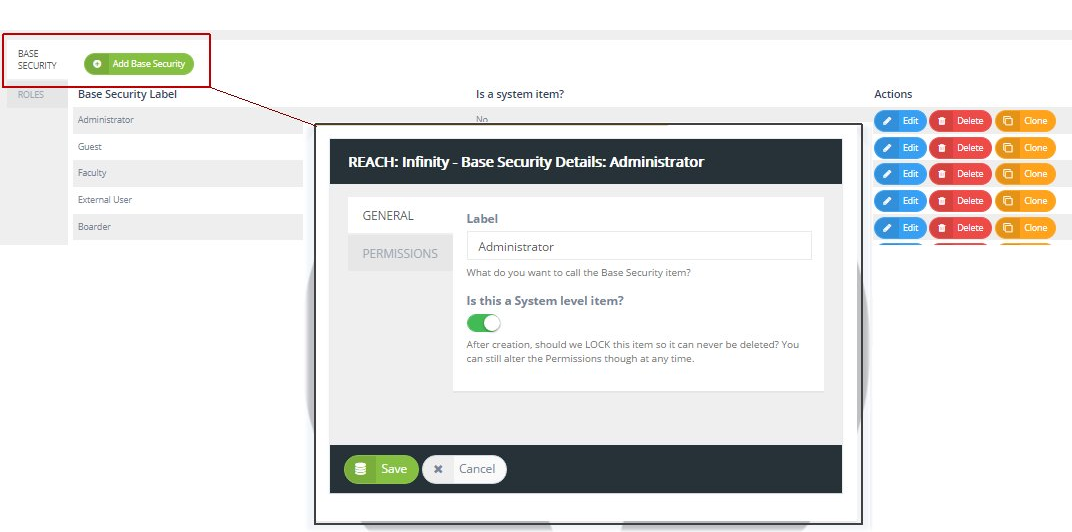
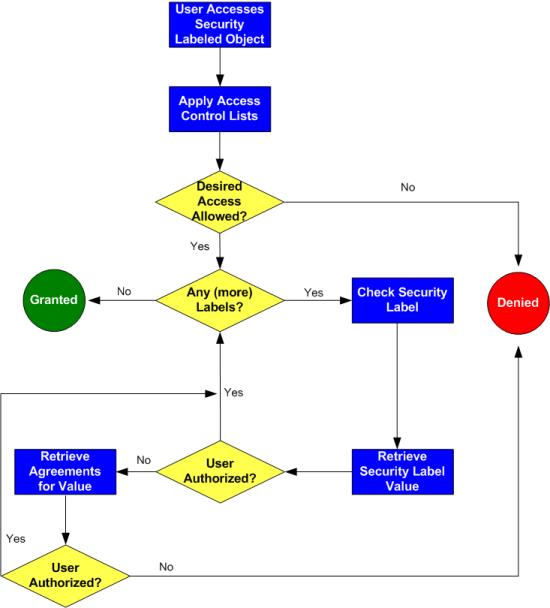
LBAC security labels - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to ... Label-Based Access Control - IBM Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting ...
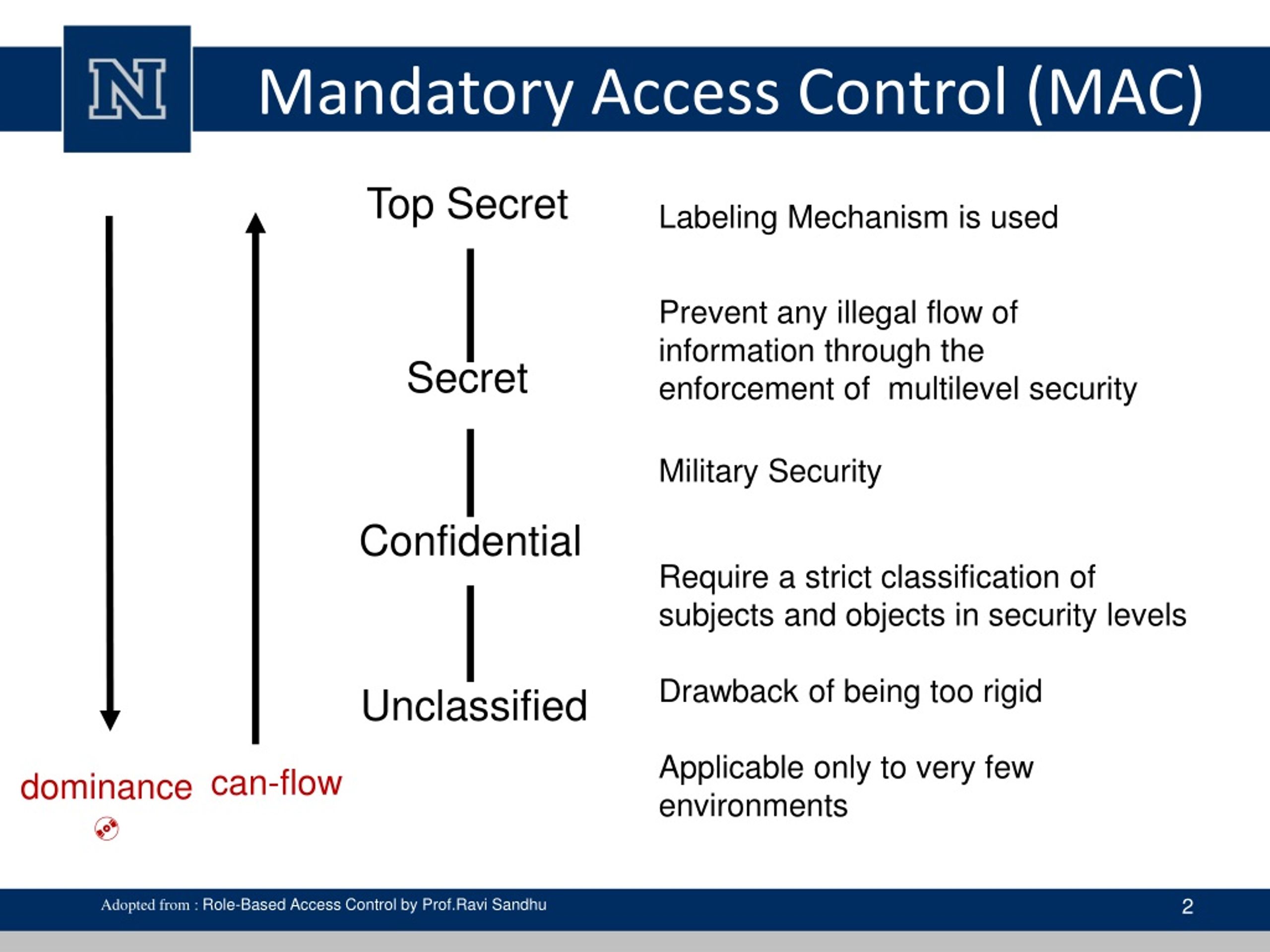
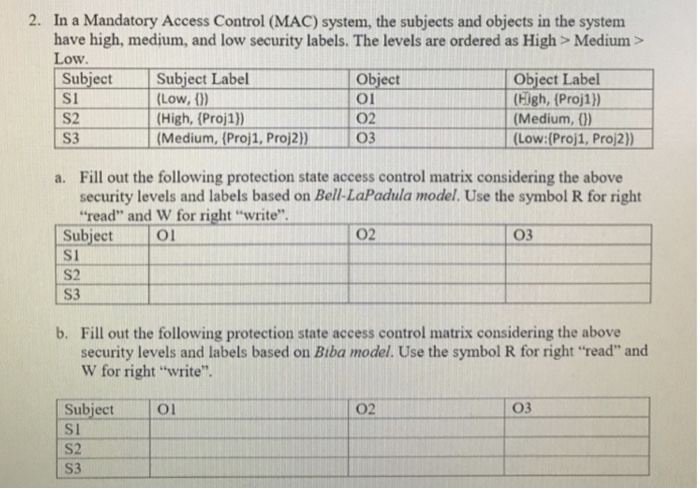
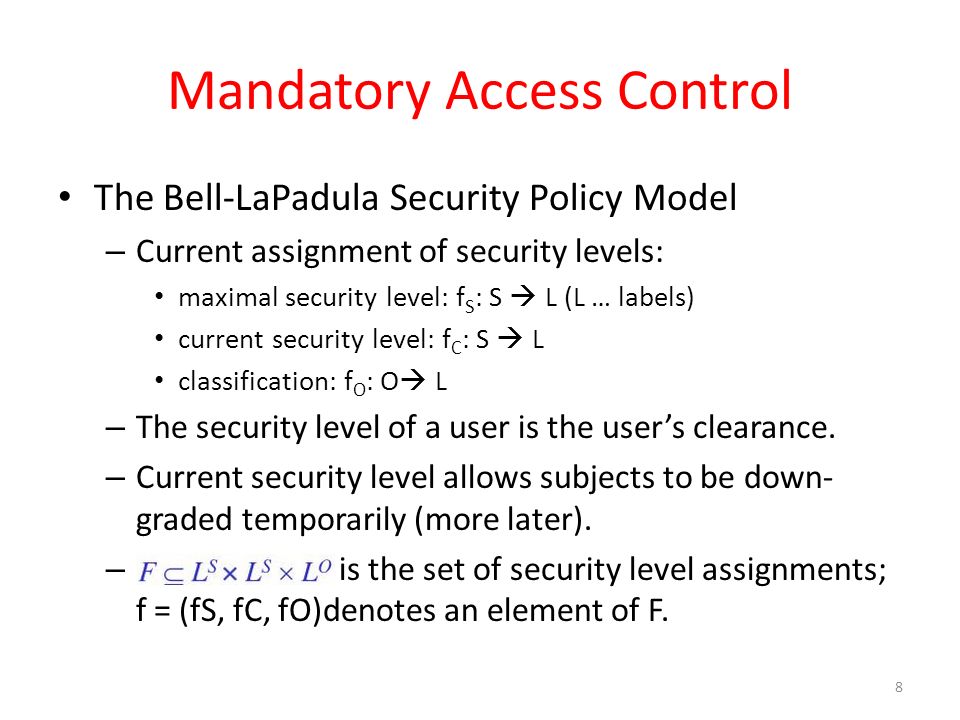
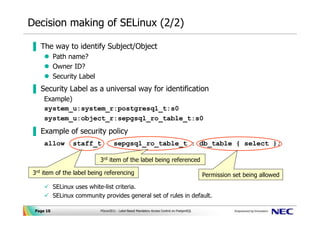
Security Labels and Mandatory Access Control (MAC) - IBM Mandatory Access Control (MAC) is a security policy that governs which subjects can access which objects, and in what way, based upon certain rules.

Security labels access control
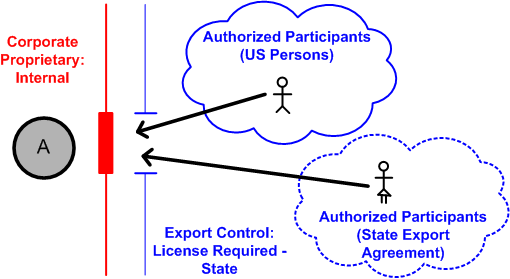
Label-based access control (LBAC) overview - IBM A security administrator allows users access to protected data by granting them security labels. When a user tries to access protected data, that user's ... How security labels control access - IBM Security labels rely on security label components to store information about the classification of data and about which users have access authority. Security Labels and Access Control - PTC Support Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not ...
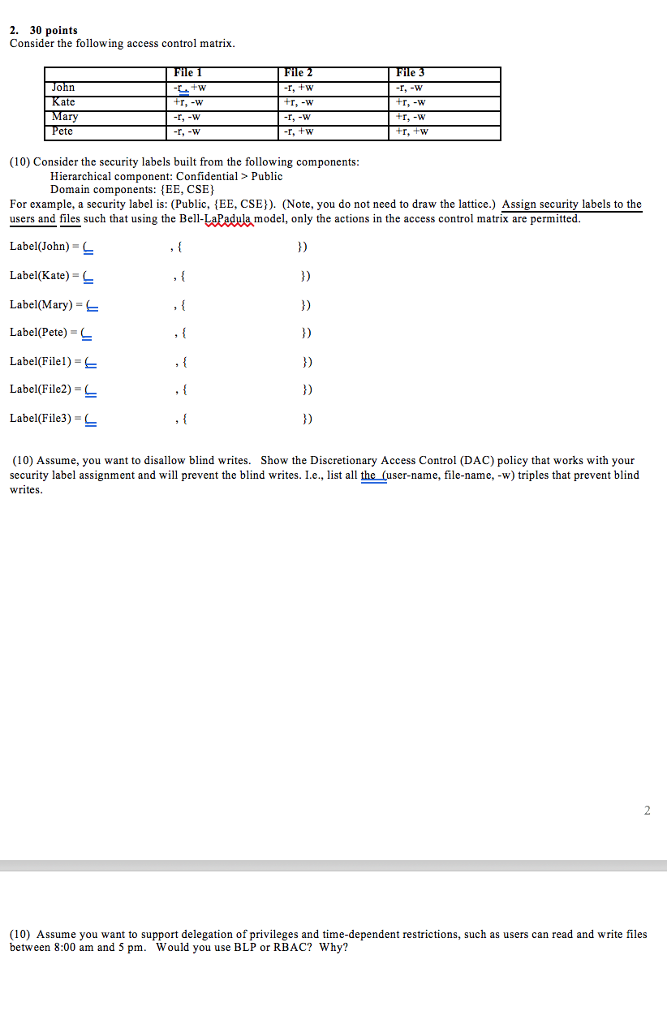
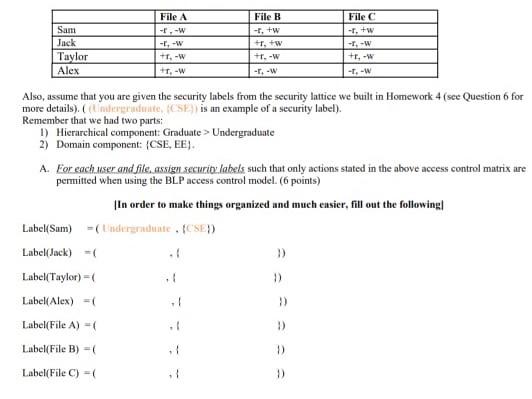
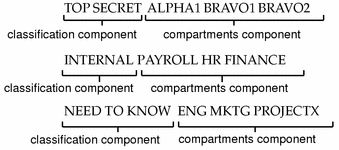
Security labels access control. Security label components - IBM The elements of these components are used to define security labels, which control access to protected tables. Security label components represent any ... Access Control using Security Labels & Security Clearance Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an ... Security Labels and Access Control - PTC Support Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not ... How security labels control access - IBM Security labels rely on security label components to store information about the classification of data and about which users have access authority.
Label-based access control (LBAC) overview - IBM A security administrator allows users access to protected data by granting them security labels. When a user tries to access protected data, that user's ...

Keychain Sticker Card Label Key IC Keychain Access Control EM Keychain Token Portal Reader 13.56MHZ RFID Multi-color Optional

Notice Security Measures for access control Maritime Sign LABEL DECAL STICKER Sticks to Any Surface 10x7





!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)














Post a Comment for "44 security labels access control"